Cookieless Tracking For Cross-site Iframes
Updated 25 May 2021 : Added information about using this with GA4. As Google Analytics 4 does not have a mechanism to disable cookie storage, only the second solution (send dataLayer events from iframe to the parent) described in this article will work for GA4.
Here I am, back with <iframe> and cross-domain tracking . I’ve published a couple of articles before on the topic, with my upgraded solution being the most recent one. These articles tackle the general problem of passing the Client ID from the parent to the <iframe> .
By doing so, the <iframe> can take the Client ID from the frame URL and create the _ga cookie in the <iframe> , allowing hits from the parent and the <iframe> to use the same Client ID. Great.
However, there’s a catch that’s become more and more troubling with the increase of browsers’ tracking protection mechanisms : if the <iframe> loads content cross-site , the browser must allow cookie access in third-party context . In other words, if the browser blocks third-party cookies , the <iframe> will not be able to write the cookie, and Google Analytics tracking will fail .

This article offers two solutions to this problem.
The first is that it sends the Google Analytics Client ID from the parent to the <iframe> using window.postMessage , and the child frame can poll for this information on every page, meaning cookies are not needed to store the Client ID.
The second solution is that the child frame actually sends every single dataLayer message to the parent, so that the child frame doesn’t have to track anything by itself. The parent handles the tracking for the child frame instead.
Using window.postMessage is more robust than the link decoration of my earlier proposals, because it doesn’t force a reload of the frame, nor does it require the child frame to support cookies. It’s a bit more elaborate to set up, however.
Warning! I’m not kidding about that last statement. Setting this up requires quite a bit of custom code, and you’re working with bilateral communication between two windows. Please read this article carefully so that you understand what’s going on before copy-pasting any code to your Google Tag Manager container(s).
Table of Contents
The Simmer Newsletter
Subscribe to the Simmer newsletter to get the latest news and content from Simo Ahava into your email inbox!
What exactly is the problem?
Glad you asked!
When a page loads an <iframe> from a cross-site origin, that frame is loaded in a third-party context, and any access to browser storage from within that <iframe> will require the browser to allow third-party cookies for the <iframe site.
A key term here is cross-site . This means that the top privately-controlled domain name of the <iframe> is different from that of the parent page.
In the examples below, the top privately-controlled domain name is in italics.
- www. simoahava.com
- www. gtmtools.com
- www. ebay.co.uk
- sahava.github.io
- analytics. google.com
If any one of the sites above loaded any other site from the list in an <iframe> , that content would be loaded cross-site, and any cookie operations within the embedded page would require third-party cookie access.
The following examples are all same-site , even if they are cross-origin:
- simoahava.com
- blog. simoahava.com
- tracking.endpoint. simoahava.com
Any communication between pages from the list above would happen in a same-site (or first-party) context, and cookie access would not be restricted.
As I mention in the introduction, this is only going to spell doom for tracking within embedded content due to how browsers implement tracking protections.
Even though Google recently made a veritable non-announcement by saying they’ll phase out third-party cookies by 2022 , Google Chrome will actually make things harder for cross-site cookie access much, much sooner.
Chrome v80 (released on February 4, 2020), enforces SameSite cookie restrictions , which means that if a cookie should be accessible in third-party context, it requires the SameSite=None and Secure flags set. By default, these are not set.
You can set those flags with the cookieFlags setting, but do note that this only fixes the “problem” for Google Chrome. It doesn’t make those cookies work in browsers that block third-party cookies.
Luckily, there’s a way around this.
We can ignore cookies altogether.
Solution 1: Pass the Client ID from the parent to the child
NOTE! As there is currently no mechanism to disable cookie storage from Google Analytics 4 deployments, this solution will only work for Universal Analytics. For GA4, you need to use Solution 2 below.
Let’s take a look at another celebrated illustration from yours truly:
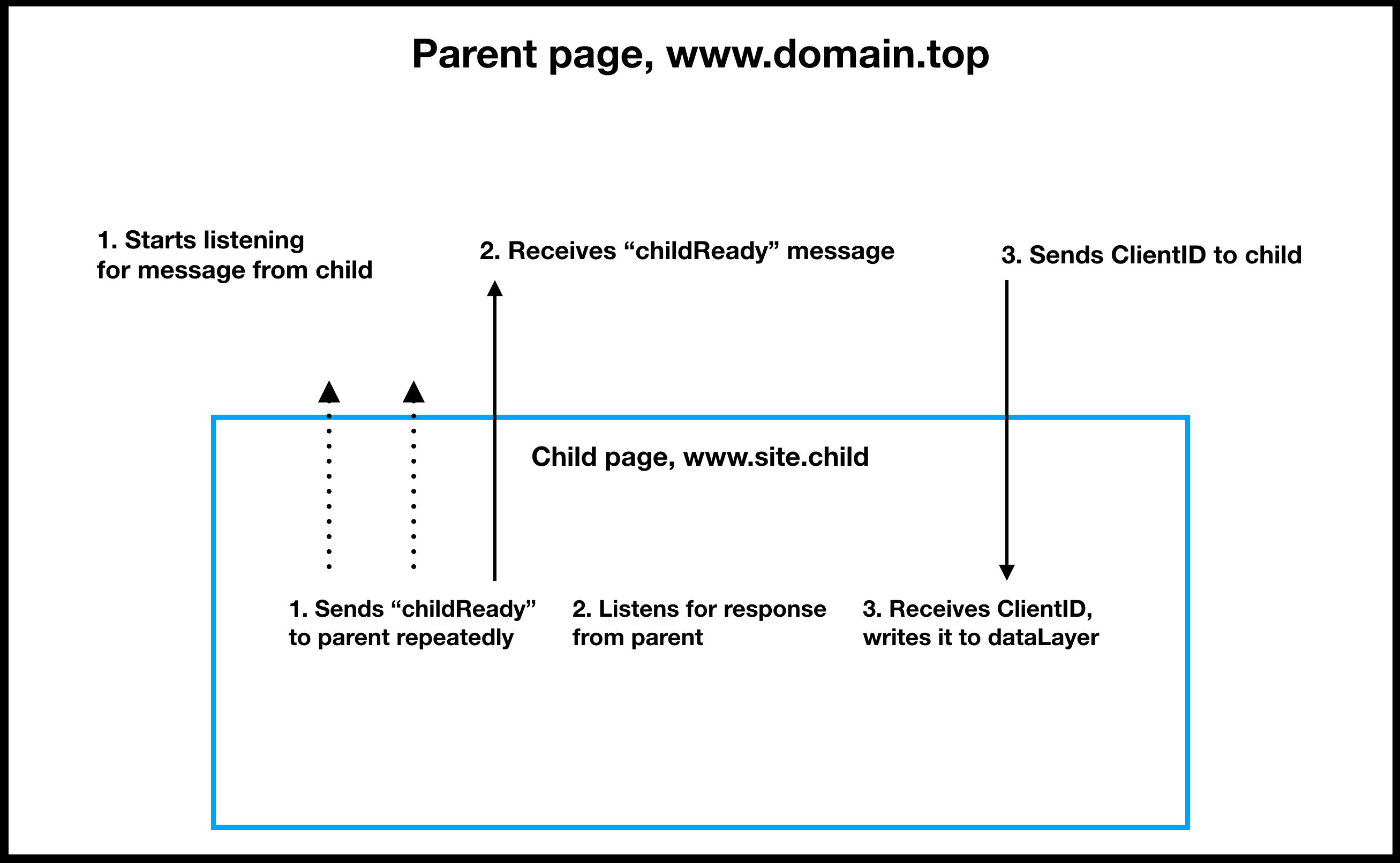
There are many potential race conditions in the mix, so some precautions need to be taken. Here’s how the parent page works:
- The parent page starts listening for messages from the <iframe> as soon as Google Tag Manager loads.
- Once the parent page receives the childReady message, it starts polling for the Google Analytics tracker until a maximum timeout is reached.
- As soon as the Google Analytics tracker is available, the parent page sends the Client ID back to the <iframe> .
And here’s how the <iframe> page reacts:
- The <iframe> page starts sending the childReady message as soon as Google Tag Manager loads.
- Once the parent page responds with the Client ID (or a timeout is reached), the child page stops sending the message.
- The child page writes the Client ID into dataLayer .
So now we know how the Client ID will be passed to the <iframe> , but that’s not enough, yet.
Every single Google Analytics tag in the <iframe> must be configured to work with this setup!
More specifically, they all need two fields set, preferably in a Google Analytics Settings variable :
- storage set to none to avoid the tracker failing if it can’t write the Client ID cookie.
- clientId set to the value from the dataLayer .
We’ll get to these shortly , don’t worry.
Solution 2: Forward all Data Layer messages from child to parent
If you don’t want to do any tracking within the <iframe> (I don’t blame you), you can actually delegate tracking to the parent by sending all dataLayer messages to the parent for processing.
This is the only viable solution for tracking cross-site iframe traffic with GA4.
This means the parent page would manage tags for both the parent page’s native interactions as well as those that happen within the <iframe> .

The process is almost the same as with the first solution. Here’s how the parent page works:
- Once the parent page receives the childReady message, it responds with a parentReady message.
- If the child frame sends a message in dataLayer -compatible format, the parent page pushes this message into its own dataLayer .
On the <iframe> , this is what happens:
- Once the parent page responds with parentReady , the child frame “hijacks” the dataLayer.push() method, and sends all the messages passed to it over to the parent page.
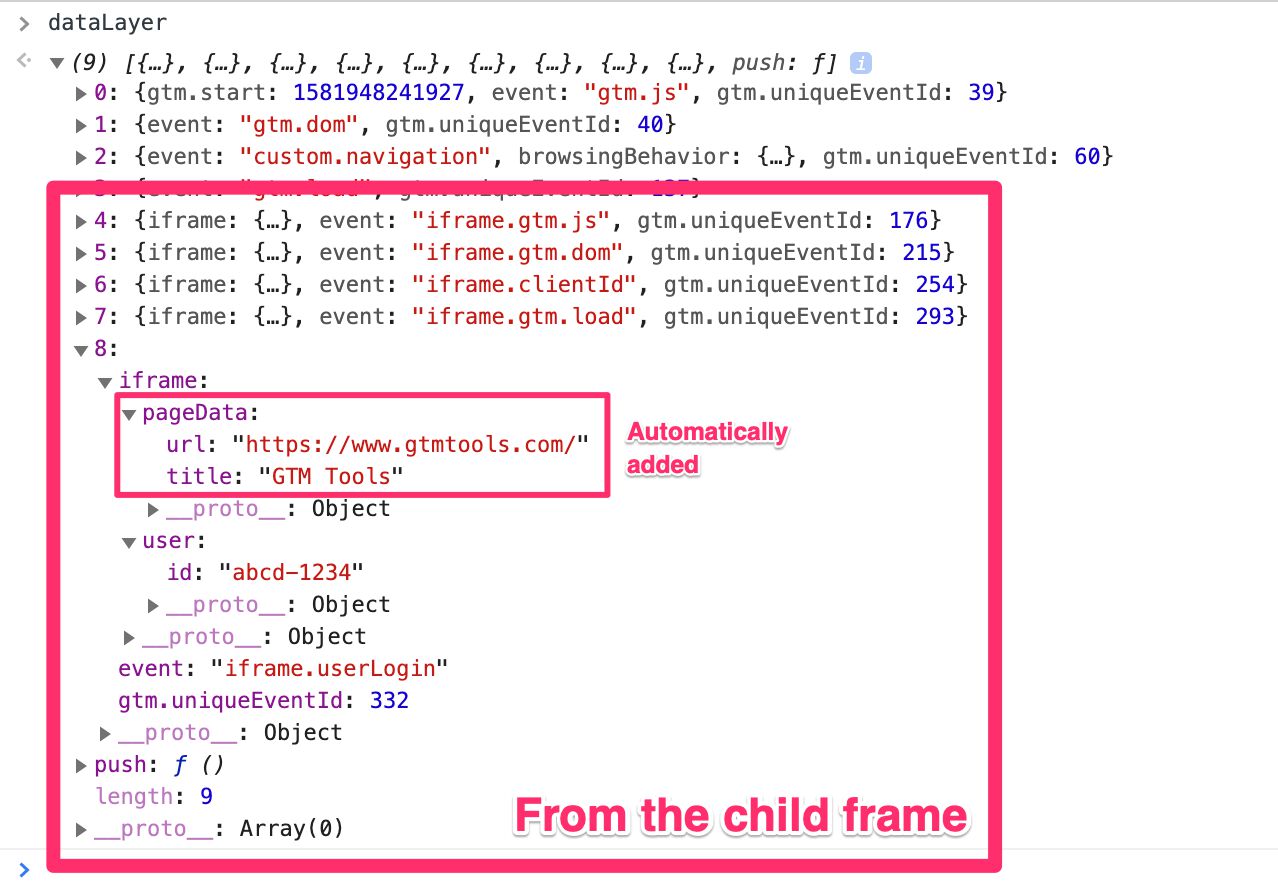
The messages from the child frame are namespaced to keep them separate from the parent’s “native” dataLayer messages, and they include some metadata about the <iframe> (mainly the URL and title).
The parent page setup
This article combines both solutions into a single set of Custom HTML tags, one for the parent page and one for the child <iframe> .
On the parent page, i.e. the page sending the Client ID to the <iframe> and waiting for the messages sent from the child, you need to create a Custom HTML tag that fires on a Page View trigger. You can use the All Pages trigger if you wish, but you might as well create a Page View trigger that only fires on pages where you know the <iframe> to exist.
The Custom HTML tag
The Custom HTML tag itself should contain the following code:
There’s quite a lot happening here, so let’s walk through the code! If you don’t care about this deep-dive, you can skip right to how you might need to configure the parent page container to support the message forwarding setup.
Configuration
First, there’s the configuration stuff:
The trackingId should be set to the Google Analytics tracking ID of the tracker whose _ga cookie you want to use. This is because there might be multiple GA cookies each storing the Client ID for a different Tracking ID. If you’re unsure, just type your regular tracking ID as the value of the trackingId variable.
Set maxGATime to the maximum amount of time that the page waits for Google Analytics to load. You can certainly set this a lot higher than 2000 (2 seconds) if you want, but I would recommend against indefinite polling.
The trackingId and maxGATime settings are only relevant for Universal Analytics. If tracking to GA4, you do not need to change these from their default values.
Set the childOrigin to the origin of the <iframe> you want to send the data to. The origin is everything in the URL up to the first path slash. So, if the URL is https://www.simoahava.com/my-home-page/ , the origin would be https://www.simoahava.com .
It’s important to not have the trailing slash, as that’s part of the path component and not the origin .
The listener
On the last line of the main code block, we add the message listener:
This means that when an <iframe> sends a postMessage to the parent page, the listener fires and executes the postCallback function.
First, if the message retrieved was not expected (e.g. coming from a different <iframe> or has the wrong content), the callback stops execution.
If the message was from the <iframe> , the first thing that’s done is notify the child frame that the parent has received the message and is ready to start bilateral communication.
Next, a window.setInterval starts polling the parent page every 200 milliseconds up to the default of 2 full seconds. With each poll, the script checks if the Google Analytics tracker has been created. If it has, the script takes the clientId from the tracker, and sends it back to the <iframe> using event.source.postMessage() . After this is done, the polling is manually stopped to avoid having the Client ID being sent multiple times to the <iframe> .
In essence, the parent page needs to wait for two things:
- For the child page to signal it is ready to receive messages.
- For the Google Analytics tracker to be available, so that the Client ID can be grabbed from it.
The last code block checks if the message from the child frame contains an object with the event property, in which case it pushes this entire object into the parent page dataLayer .
Configuring the message forwarding system
The parent page listens for dataLayer messages forwarded from the embedded <iframe> . You can create tags, triggers, and variables that react to these messages.
All triggers will be of type Custom Event trigger . That’s because all the events sent from the frame will be appended with the iframe. prefix - even those without an event value (they’ll be sent as iframe.Message ). So, if you want to fire a tag when a link is clicked in the <iframe> , the trigger could look like this:
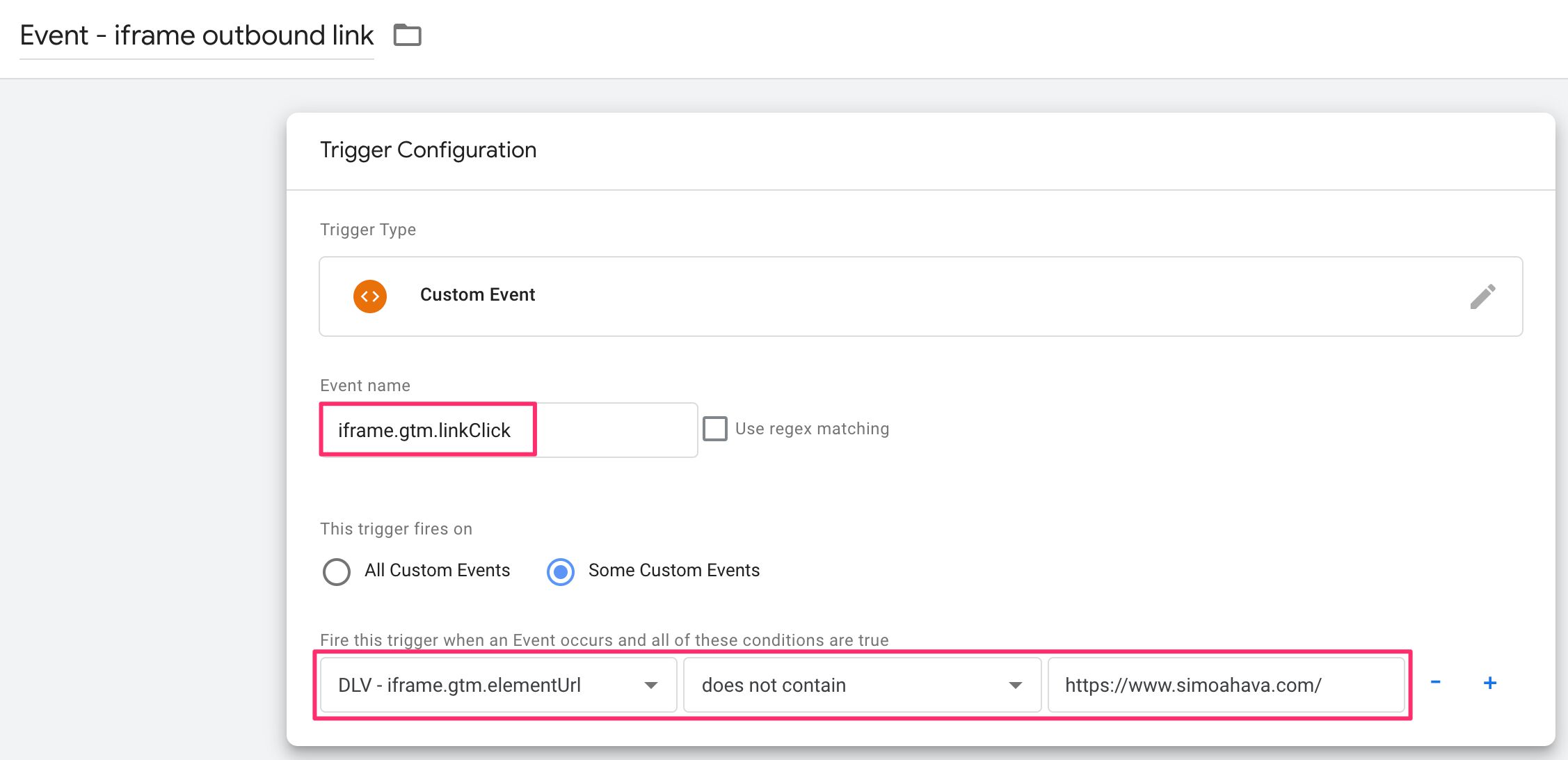
It requires quite a bit of manual configuration to get the whole thing up and running. But it can make your whole setup run much smoother, as you won’t need to embed any extra code within the <iframe> .
Each message sent from the <iframe> is automatically enhanced with some page-level information:
If you want to update your parent page tags to use the <iframe> page-level data, you need to create Data Layer variables for iframe.pageData.url (the URL of the <iframe> page) and iframe.pageData.title (the page title).
Once you have all these configured, you’re ready to configure the <iframe> page!
The embedded (child) page setup
This is where things get tricky. In this guide, we’re covering a fairly typical use case where the <iframe> content is only ever interacted with as an embed. So there’s no scenario where the user would visit the page loaded in the <iframe> in a first-party or top-frame context. I’ll briefly discuss that scenario later as well, but for now let’s assume that the page in the <iframe> is only accessed as an embedded element.
You’ll need to do three things in the Google Tag Manager container of the <iframe> page.
- Create a Custom HTML tag that communicates with the parent page.
- Update the settings for all of your Universal Analytics (and App+Web while you’re at it) tags.
- Update the triggers for your Universal Analytics tags so they don’t fire until they’ve received the Client ID from the parent.
Create a new Custom HTML tag, and set it to fire on the All Pages trigger. If the <iframe> is a single-page app, you should still only fire the Custom HTML tag on the All Pages trigger, and not with every SPA page change, for example.
Here’s what you should copy-paste into the tag:
The following chapters will walk through this code. You can skip right to configuring the Google Analytics tags if you don’t care about the walkthrough.
This is the first code block:
First of all, if the page is not loaded in an <iframe> , the code does not and should not execute at all. There’s no parent page to communicate with, so executing any of the following code would be unnecessary.
You can set sendDataLayerMessages to false if you don’t want to forward the dataLayer messages from the child to the parent. This is useful if you’re comfortable with tracking everything within the <iframe> itself, and don’t want to bother with setting up the corresponding tags in the parent page.
The dataLayerMessagePrefix value is what will be used to namespace the dataLayer messages that are forwarded from the child to the parent (if you haven’t disabled forwarding per the previous paragraph).
The parentOrigin should be set to the origin of the parent page, i.e. the page to which the messages are sent. Remember, origin is everything from the protocol to the first slash of the path component. In other words, the origin of https://www.simoahava.com/some-page is https://www.simoahava.com .
Finally, the maxTime is how long the <iframe> tries to send the childReady message to the parent before it stops.
The child frame polls the parent page with the childReady message to signal it’s ready for the bilateral communication to start.
It runs every 200 milliseconds until the maximum poll time (2000 milliseconds by default) is reached.
At the same time as it starts polling, a postMessage listener is also initiated. This listener waits for two things:
- The parent to signal parentReady , so that the <iframe> can start forwarding its dataLayer messages to the parent .
- The parent to return a Client ID string, so that the <iframe> can use this in Google Analytics tags.
If the parent sends a clientId message, then the page pushes this data into dataLayer , and Google Analytics tags firing in the <iframe> can utilize this information in their settings.
If the parent sends a parentReady message, the <iframe> stops sending the childReady message. Then, it fires up the dataLayer message forwarder (unless the user has chosen to prevent this).
The message forwarder
The forwarder comprises two methods: createMessage(obj) and startDataLayerMessageCollection() .
Without going into too much detail, the basic setup is this:
- The createMessage() method is a utility that wraps the dataLayer message from the <iframe> page with the prefix configured in the beginning of the Custom HTML tag ( "iframe" ) by default. This prefix is used with the event name (so gtm.js becomes iframe.gtm.js ) as well as with the object itself (so {key: 'value'} becomes {iframe: {key: value}} ).
- The createMessage() method also automatically adds a pageData object which contains the url and title of the page in the <iframe> .
- The startDataLayerMessageCollection() method first sends everything in the dataLayer array collected thus far to the parent.
- Then the method rewrites the dataLayer.push function to send everything pushed into dataLayer to the parent page as well.
In other words, everything added to the dataLayer array within the <iframe> is forwarded to the parent page, so that the parent page can handle tracking of interactions and events within the <iframe> as well.
For example, here’s how the forwarded transpiles and sends a dataLayer message to the parent page.
Google Analytics tags
If you do want to collect data to Google Analytics from within the <iframe> page, you need to configure all your Google Analytics tags with the following settings:
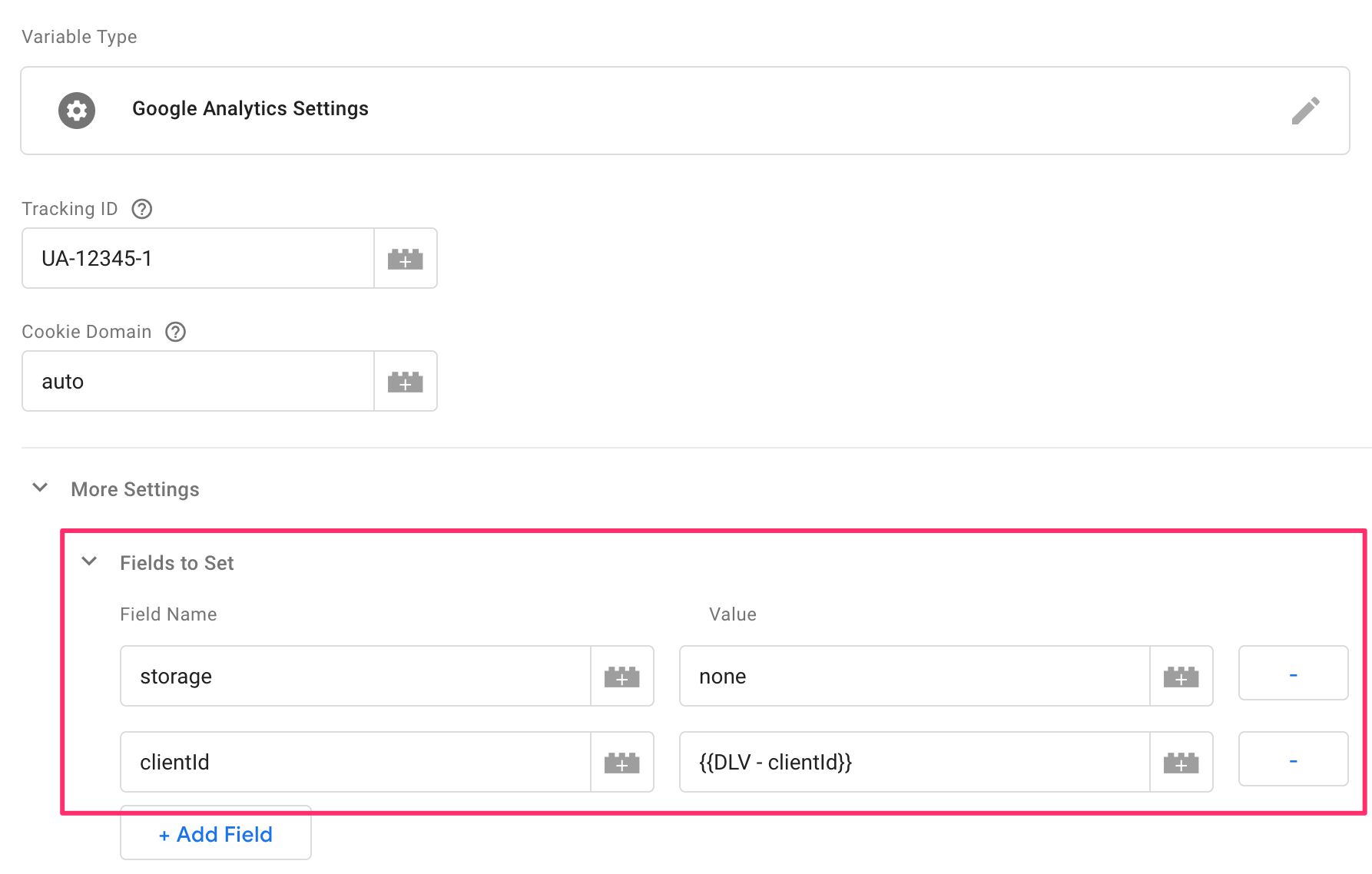
As the <iframe> will no longer use cookies to persist the Client ID, you need to set the storage field value to none .
Then, because the child frame uses the Client ID pushed into dataLayer by the message listener, you’ll need to update the clientId field to use a Data Layer variable for clientId . It should look like this:
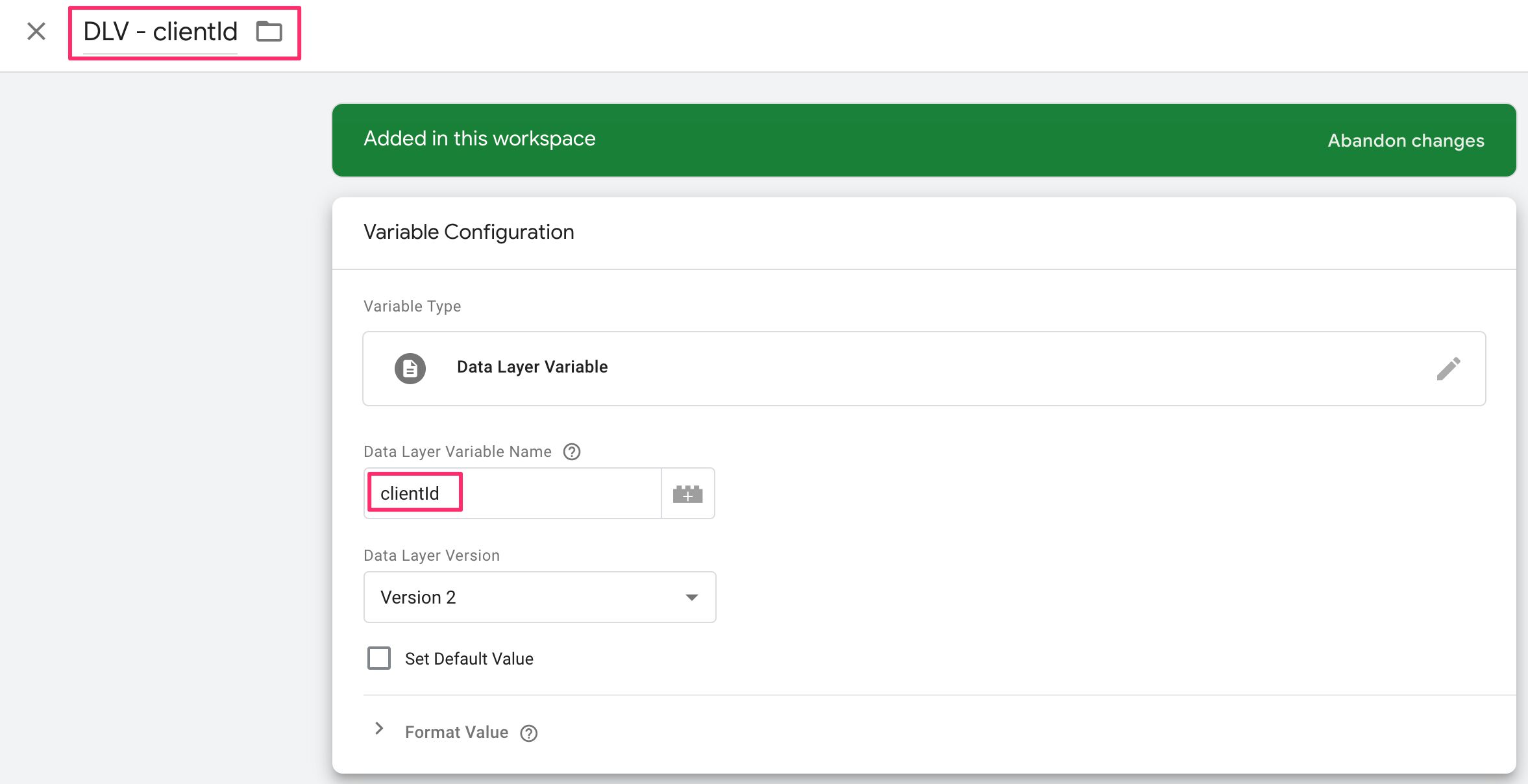
None of your tags should fire if the Client ID is not yet available. You can use the clientId in a Custom Event trigger to fire your tags when Client ID has been pushed to dataLayer .
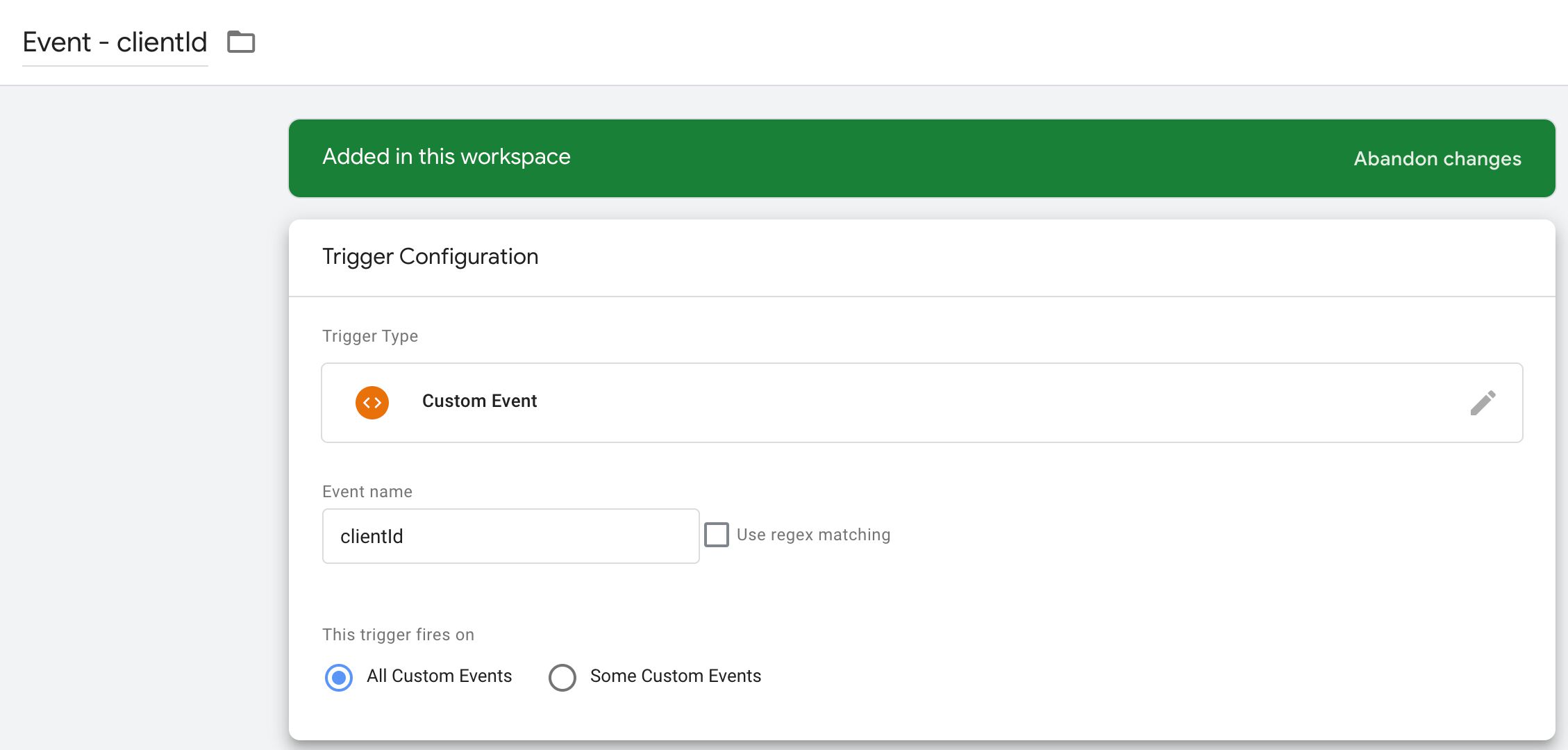
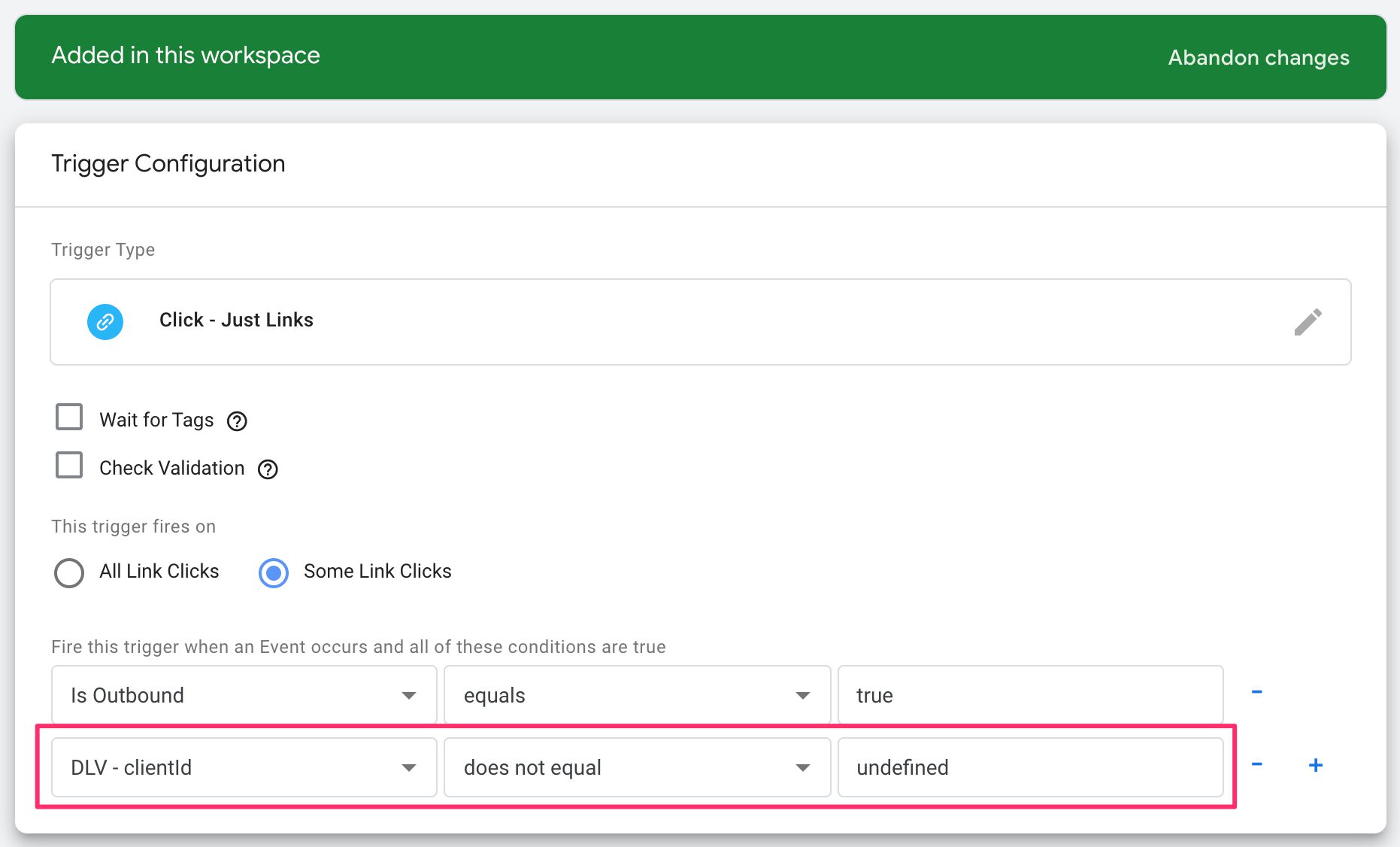
You can also update your existing triggers to not fire until clientId has a valid value.
Multi-purpose container
One important caveat to note is that if you set up all your tags per the instructions in the previous chapter, then the container running in the <iframe> will not function properly if the page is visited directly as a top-level page, i.e. not as an embed.
I would generally recommend to avoid mixing too many use cases in a single container. It might be wiser to create a different container for scenarios where the page is visited directly, and have the developers update the site code to load the correct container, depending on whether the page is embedded in an <iframe> or not.
However, if you do want the container to cater to different use cases, then a good idea is to create a separate set of tags for when the page is accessed in the top frame vs. when the page is accessed as an embed.
You can use a simple utility variable to check if the page is accessed as an <iframe> or not. This Custom JavaScript variable returns true if the page is NOT in an <iframe> and false otherwise.
You can then check for this variable value in your tags, triggers, and variables, to make sure that tracking is configured correctly depending on how the page is accessed.
This has been a difficult article to write, and I feel a bit embarrassed to leave so much work to you, my noble reader.
The thing is - working with this type of a bilateral messaging setup requires both the parent page and the <iframe> page to be in sync. The Custom HTML tags I’ve designed have been built to naturally reject race conditions, but it’s possible you’ll need to modify one or the other (or both) to make things work on your site.
Over the course of my career, and especially over the time I’ve been blogging about Google Tag Manager, trying to perfect tracking of <iframe> elements has been my personal Mount Everest. Cross-site tracking of embedded content has take over my life to such an extent that I’m losing sleep and seriously considering hunting down Ibrahim or Isabella Frame, or whoever the person is who thought the <iframe> is a great addition to the HTML spec.
Regardless, it’s still such a common use case on the SaaS- and micro service -rich web to embed cross-site content. Naturally, there’s an incentive to know what happens in these <iframe> blocks that I consider the time I’ve spent trying to solve this particular riddle to be almost worthwhile.
Anyway, I expect and hope that you have comments and/or questions about this setup. Let’s continue the discussion in the comments of this article, thank you!
- Share on Facebook
- Share on Twitter
- Share on LinkedIn

Updates to the Storage Access API
Feb 10, 2021
by John Wilander
@johnwilander
The Storage Access API allows third-party web content to ask for permission to get access to its unpartitioned storage, typically in order to authenticate the user. In the case of Safari and WebKit, using the Storage Access API enables cookie access under Intelligent Tracking Prevention .
This blog post covers two changes to the Storage Access API in Safari and WebKit as well as a how-to guide on adoption based on questions we’ve been asked the last two years.
Changes to API Functionality
iOS and iPadOS 14.5, and macOS Big Sur 11.3 betas feature two sought after changes to the Storage Access API in Safari and WebKit – per-page storage access and support for nested iframes. Both of these changes were driven by the standards process in W3C Privacy CG .
Per-Page Storage Access
If a request for storage access is granted to embedee.example , access is now granted to all embedee.example resource loads under the current first party webpage. This includes sibling embedee.example iframes but also other, non-document resources.
Nested Iframes Can Request Storage Access
Imagine a webpage embedding a cross-site iframe from embedeeOne.example which in turn embeds a cross-site iframe from embedeeTwo.example which makes the latter a so called nested iframe. As of this release, nested iframes such as embedeeTwo.example are also allowed to request storage access. Note that we may require first parties to explicitly delegate this capability through Permissions Policy at a later stage. Mozilla has expressed an interest in such control.
How To Use the Storage Access API
For the purposes of this guide we will use the domains social.example for the embedded content in need of cookie access and news.example as the first party website embedding social.example .
First, Cross-Site Iframes Call the API
The Storage Access API is called from inside cross-site, or third-party, iframes. You don’t have to call the API if your website is first party and first party websites cannot call the API on behalf of third-parties.
How-To #1: Meet and Greet the User as First Party
If you want to make use of the Storage Access API as a third-party, you first need to take these steps as a first party:
- Make sure you are using regular browsing mode, i.e. not Private Browsing. We will cover Private Browsing at the end of this guide.
- Take the user to your domain as first party. This is your website showing itself and giving the user a chance to recognize your brand and domain name. Recognition is important since the prompt for storage access features your embedded iframe’s domain. In our example, this is taking the user to a webpage with social.example in the URL bar, either though a navigation or a popup.
- Have the user interact (tap, click, or use the keyboard) with your website as first party. This tells the browser that the user has actually seen and used the site. Note : Navigating to and from your website in a redirect without user interaction does not count. Formally, WebKit’s requirement is user interaction as first party the last 30 days of browser use. Being granted storage access through the Storage Access API counts as such user interaction. In our example, this is having the user tap/click on the webpage with social.example in the URL bar.
- Set cookies when you are first-party. This establishes the website as “visited” for the purposes of the underlying cookie policy. Third parties without cookies cannot set cookies in Safari and never have since Safari 1.0 in 2003. This means you cannot use the Storage Access API as third-party until you have set at least one cookie as first party. In our example, this is setting cookies for social.example with social.example in the URL bar.
The above requirements are there to make sure the sometimes 50-100 embedded third-parties on a single webpage cannot all prompt the user for storage access, only the ones the user has visited and interacted with can.
How-To #2: Use the Storage Access API as Third Party
Once you have had the user interact with your website as first party and have set cookies as first party, you are ready to make use of the Storage Access API.
- In shipping Safari, your cross-site iframe that is about to request storage access must be a direct child frame of the top frame. Nested iframes can request storage access as of iOS 14.5 and macOS 11.3 (currently in beta).
- Make your cross-site iframe call document.hasStorageAccess() as soon as it’s rendered to check your status. Note : Don’t call this function upon a user gesture since it’s asynchronous and will consume the gesture. Once the user gesture is consumed, making a subsequent call to document.requestStorageAccess() will fail because it’s not called when processing a user gesture. In our example this is social.example ‘s iframe.
- If document.hasStorageAccess() returns false, your iframe doesn’t have storage access. Now set an event handler on elements that represent UI which requires storage access and make the event handler call document.requestStorageAccess() on a tap or click. This is the API that requires a user gesture. In our example this is social.example ‘s iframe calling the API.
- Render the page with your cross-site iframe. Tap or click on an element with an event handler in the iframe. In our example this is rendering a page from news.example with the social.example ‘s iframe and clicking on an element in the social.example iframe’s document.
- If the user has not yet opted in to storage access for social.example under news.example there will now be a prompt. Choose “Don’t Allow” in the prompt. Tip : Don’t choose “Allow” yet because it’ll be remembered and you’ll have to delete browser history to reset it. If you are not getting the prompt, you either have not gotten user interaction as first party and set cookies for social.example yet (see How-To #1) or you have already chosen “Allow” earlier which is remembered.
- Test the behavior for the “Don’t Allow” case. You can do it repeatedly. Do it until you’re happy with how your code handles it. Note that when the user chooses “Don’t Allow” in the prompt, their user gesture is consumed and any further API calls in your iframe that require a user gesture will have to get the user to tap or click again. We’ve deliberately designed it this way to make sure that an explicit deny from the user doesn’t trigger further privileged API calls from the iframe. The user should at this point be able to continue with other things.
- Now tap or click the iframe again and this time choose “Allow” in the prompt. This should open up cookie access on resolution of the promise.
- Test the behavior for the “Allow” case. Note that when the user chooses “Allow” in the prompt, their user gesture is preserved and any further API calls in your iframe that require a user gesture can go right ahead. We’ve deliberately designed it this way so that when you get access to cookies and note that the user is not in the desired state, such as not logged in, you can open a popup or navigate them to your website without further user gestures. In our example this would be a popup or navigation to social.example .
- Now reload the webpage. This will reset your per-page storage access. Tap or click the iframe to trigger the call to document.requestStorageAccess() . This should open up cookie access without a prompt since the user has already opted in and that choice is remembered.
- Finally test the flow in Private Browsing Mode. In that mode, the user must interact with your website as first party (see How-To #1) in the same tab as where you later request storage access as third-party. This is because Private Browsing Mode uses a separate ephemeral session for each new tab the user opens, i.e. the state of those tabs are separate. The rest should work the same as in regular mode.

‘Prevent Cross-Site Tracking’ in Safari Explained
Safari has an important privacy feature to prevent cross-site tracking. Regardless of your device — Mac, iPhone, iPad or Windows PC — you will see an option to turn off or on this feature in Safari’s settings. This is enabled by default. You may wonder what this option really means and what really happens if you turn it on or off. In this article, I will explain what “prevent cross-site tracking” does, if you should turn it on or off and then how to enable or disable it.
What is cross-site tracking
Before I start, I should mention that all major browsers like Firefox, Mozilla or Chrome offer similar features. This is because it is an important feature, and if you value your privacy, you should know about it.
Let’s give an example. Say you visited a site, any site with ads on it which is most sites on the net. And assume that you clicked an ad on the site because it was something you were interested in. Then you leave this site 10 minutes later, then the next site you visit may show the same ad you clicked on or ads in the same category. This is because a third-party ad agency on the first site tracked you so that it could customize the ads for you. It can keep tracking you across multiple websites, and thus, the same or very similar ads may appear on the other sites you visit later based on your previous interactions. In other words, the ad agency will use this to target you. This would not occur if you enabled “Prevent cross-site tracking” in Safari because the ad agency would be prevented from tracking you.
Should you enable or disable this?
In general, you should enable this. By this, I mean turn on “ prevent cross-site tracking .” This is an important privacy feature. That is why it is enabled by default, and you should not turn it off. When you enable this, Safari will prevent trackers from following you and viewing your IP address or location details. However, there can be a few scenarios you may need to disable this. For example, some sites may be heavily dependent on cross-site tracking to operate. For example, some seat-booking websites or online learning platforms may ask you to disable this. What you can do is temporarily disable it, and then you can enable it after you are done.
What happens if you enable this
These will occur:
- When you visit a site with third-party trackers, the trackers will be blocked.
- The trackers’ cookies and website data will not be saved.
How to turn “Prevent cross-site tracking” on and off
- In Safari, click on Safari , then Settings (or Preferences if you are running an older version of macOS).
- Click the Privacy tab.
- Select the “ Prevent cross-site tracking ” box to enable this. Uncheck the box to disable it.
On iPhone or iPad:
- Tap Settings and Safari .
- Scroll down and find the “ Privacy and Security ” section.
- Toggle on (or off) Prevent Cross-Site Tracking .
Can you see the trackers?
Yes, Safari lets you view your privacy reports . These reports will include the following:
- Does the website you are visiting have any third-party trackers trying to follow you? Again most sites do.
- A summary of trackers that you have encountered in the last 30 days.
- The trackers that are blocked from following you.
- A summary of websites with the number of trackers.
Here is how to open Safari’s privacy report:
- Open Safari and visit a site like macreports.com
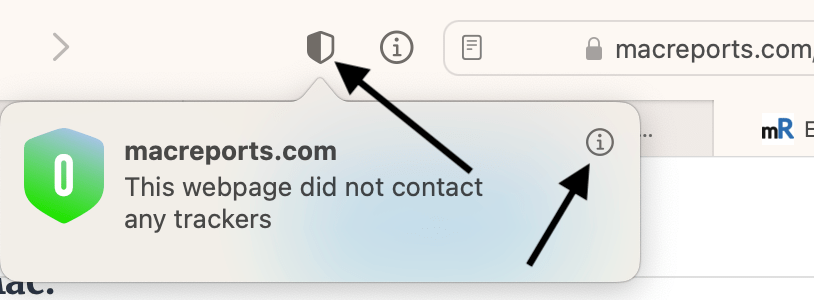
- Click the Privacy Report button located in the toolbar, usually to the left of the URL bar. This will show if the site has any third-party trackers. If you don’t see the Privacy Report button, go to the top menu bar and click on View > Customize Toolbar to add the Privacy Report button.
- Click the (i) info button to see more details.
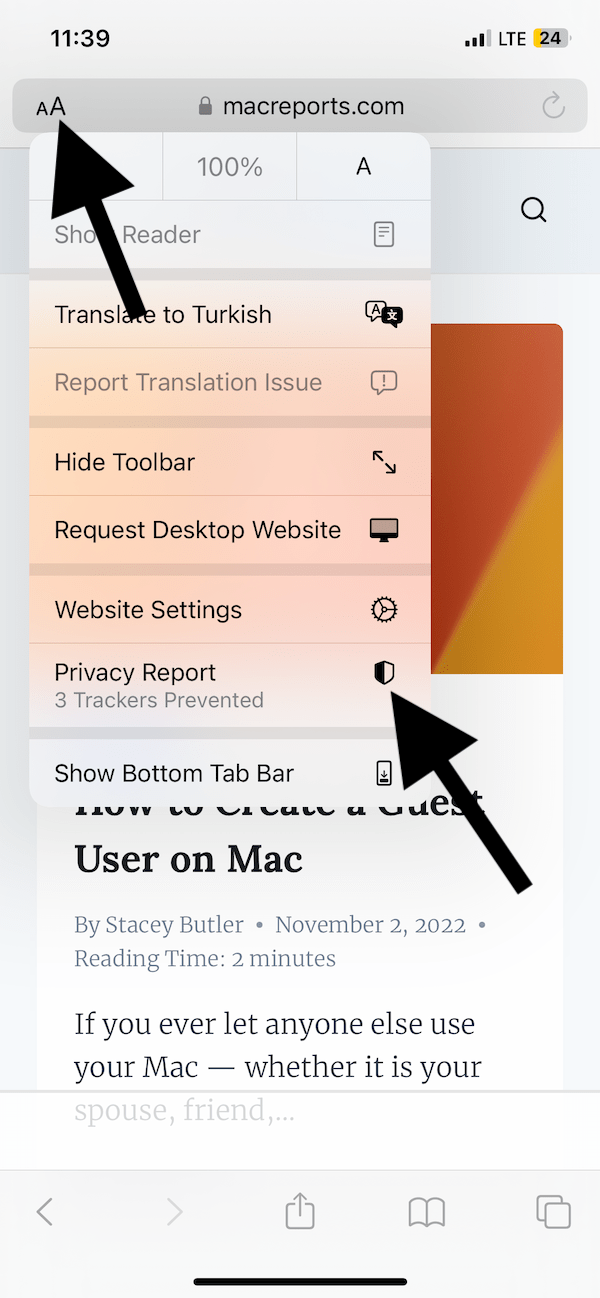
- Open Safari and visit a site.
- Tap the double AA button, which is located on the left side of the URL bar.
- Select Privacy Report .
Related articles
- Do you See ‘Privacy Warning’ in Wi-Fi on iPhone or iPad?
- How to Protect your Data and your Privacy on Mac
- How to Access Apple’s Private Relay Service
- Safari Private Browsing Button Missing? Fix (iOS)
- Safari “This Connection Is Not Private” Warning
Dr. Serhat Kurt worked as a Senior Technology Director specializing in Apple solutions for small and medium-sized educational institutions. He holds a doctoral degree (or doctorate) from the University of Illinois at Urbana / Champaign and a master’s degree from Purdue University. He is a former faculty member. Here is his LinkedIn profile and Google Scholar profile . Email Serhat Kurt .
Similar Posts
How to Save an Entire Webpage as a PDF on iPhone or iPad
There are many situations when you might want to save a webpage as a PDF. You can do this from Safari, but it isn’t really obvious how to do it. There is no…
Troubleshoot FaceTime Audio Not Working
In this article, I explain how you can troubleshoot audio issues with the quality of your FaceTime video or audio call. When you make a FaceTime call or when you connect to a…
How Do I Password Protect My Files & Folders In macOS?
This articles explains how you can password protect your folders and files on your Mac. You can assign passwords for files and folders. Everyone must enter to open the file or folder because the…
Background App Refresh, What Is It and What Does It Do?
You may have seen an option called Background App Refresh in iPhone or iPad settings. You may wonder what this option does. You may also wonder whether you should turn this on or…
Apple Music: ‘Sync Library is Off,’ Turn On?
Recently, when my Verizon cellular plan changed, my Apple Music stopped syncing on my iPhone, and I didn’t have all of the songs and albums I had downloaded. When I opened my Apple…
Will a Text Message Be Delivered if You are Blocked on iPhone?
When you send an iMessage to another iPhone user who blocked you, the iMessage won’t be delivered. From your end, the Message app will say “Sent as Text Message” underneath a green bubble,…
One Comment
I find I do need to disable this privacy feature cross site tracking for some web sites. At least in my experience disabling it tends to fix the issues.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Categories:
Safari’s Privacy Report and Cross-Site Tracking Explained
Want to find which companies are tracking you across the web? With Safari’s Privacy Report it’s easy to find that out.
Do you value your online privacy? Many major tech companies, such as Google and Facebook, rely on collecting your data to use with advertisers. But as part of Apple’s defense of user privacy, it includes a Privacy Report in Safari to help you find out exactly which websites are collecting your data, so you can learn which sites are best left alone if you want to keep your data yours.
Let’s discuss Safari’s Privacy Report and how it relates to cross-site tracking.
What Is Cross-Site Tracking?
When you browse the internet, some companies use trackers to monitor your activity across multiple websites. If you don’t have appropriate protections in place, someone is almost certainly tracking you right now.
In order to track your activity, websites may use scripts or place files called cookies on your device that uniquely identify you and send information back to the source. Advertisers can then use the harvested data to present you with targeted ads. If you’ve ever seen an online advertisement that seems eerily relevant to you and your current situation, some form of tracking is likely the cause.
Related: Ways Google Can Track You and How to Stop or View it
While not all websites attempt to stalk you across the internet, some most certainly do. Social media companies can even use Like or Share buttons that you voluntarily click to monitor your activity on other sites.
Such behavior may sound like a major privacy breach—and in some ways it is. Generally, you don’t opt in to tracking and must instead find ways to prevent the practice by using browser settings or additional security tools. Luckily, Safari has a powerful feature that should thwart most tracking attempts.
Disable Cross-Site Tracking in Safari
Here’s how to prevent cross-site tracking in Safari on Mac:
- Go to Safari > Preferences .
- Click the Privacy tab.
- Tick Prevent cross-site tracking .
For extra protection, you should also tick Hide IP address from trackers , which prevents websites from profiling you using your unique IP address . Enabling cross-site tracking prevention also grants you access to Safari’s comprehensive—and often damning—Privacy Report.
Reading Safari’s Privacy Report
When you enable cross-site tracking prevention in Safari, you activate the browser’s Privacy Report. Any time you visit a website that attempts to track you, Safari gathers information and presents it in an easy-to-read format.
By clicking the shield icon to the left of your address bar, you can see how many trackers your browser has blocked on the current page. If you click Trackers on This Web Page , you’ll see exactly what items Safari prevented from tracking you.
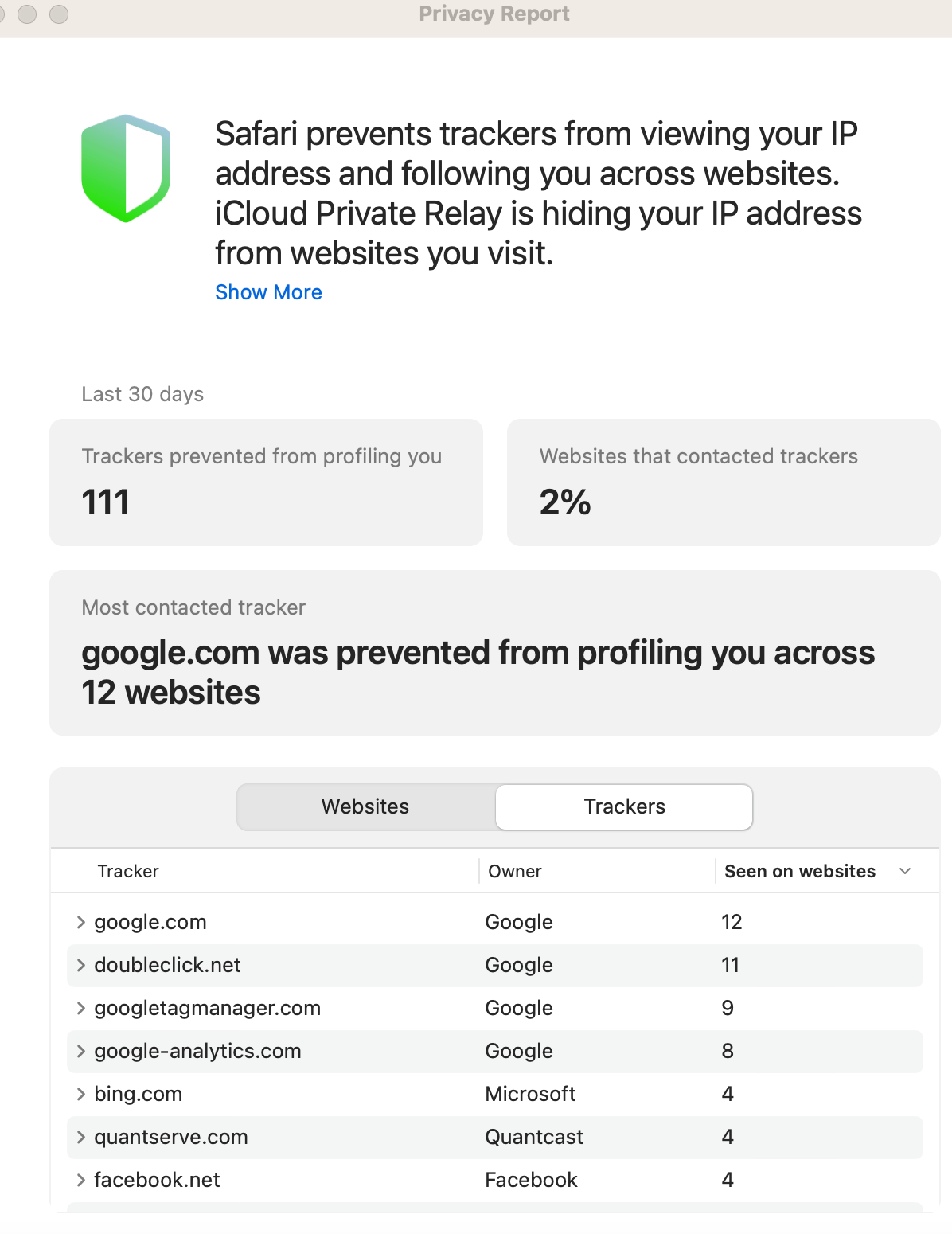
For even more info, you can click the Information (i) button to open a detailed report from the past 30 days. The Trackers prevented from profiling you section at the top of the report displays the number of trackers Safari recently thwarted. Additionally, Websites that contacted trackers shows the percentage of sites that attempted to track you.
You can either opt to view a list of Websites and their associated items or simply show the Trackers themselves. The Websites overview is great for identifying which sites are performing the most tracking. In the Trackers overview, clicking the disclosure triangle beside an entry displays the websites that attempted to stalk you with that item.
When you read Safari’s Privacy report, the amount of cross-site tracking that takes place is immediately apparent. Evidently, switching cross-site tracking off exposes you to some serious stalking across multiple sites. If you value your privacy, you’d be wise to leave all tracking prevention tools firmly in the on position.
Cross-Site Tracking Prevention Protects Your Privacy
We’ve covered the main aspects of Safari’s Privacy Report. Generally, unless you’re curious, you don’t need to pay constant attention to which trackers your browser has blocked. However, the Privacy Report is great for initially understanding how often advertisers attempt to track you and which websites are the worst culprits.
What Is Prevent Cross-Site Tracking In Safari

- Software & Applications
- Browsers & Extensions
Introduction
In today's digital age, web browsing has become an integral part of our daily lives. Whether we're shopping online, reading the news, or connecting with friends on social media, our web activities leave behind a trail of data that is often used for targeted advertising and user tracking. This practice, known as cross-site tracking, has raised concerns about user privacy and data security.
As a response to these concerns, web browsers have implemented various measures to protect users from cross-site tracking. One such browser , Safari, has introduced a feature called "Prevent Cross-Site Tracking" to enhance user privacy and security. This feature aims to limit the ability of advertisers and other entities to track users across different websites, thereby reducing the collection of personal data without consent.
Understanding the mechanisms behind cross-site tracking and the ways in which Safari addresses this issue is crucial for users who prioritize their online privacy. By delving into the intricacies of cross-site tracking and Safari's preventive measures, users can make informed decisions about their online browsing habits and take proactive steps to safeguard their personal information.
In this article, we will explore the concept of cross-site tracking, delve into the specific methods employed by Safari to prevent it, and discuss the impact of enabling this feature on the overall browsing experience. By gaining a deeper understanding of these topics, readers will be empowered to make informed choices about their online privacy and security while using Safari as their preferred web browser .
Understanding Cross-Site Tracking
Cross-site tracking, also known as third-party tracking, refers to the practice of monitoring a user's online behavior across multiple websites. This tracking is often facilitated by third-party entities, such as advertising networks and data analytics companies, which embed tracking technologies, such as cookies and scripts, into websites. These technologies enable these entities to collect and aggregate user data, including browsing history, preferences, and interactions, to create detailed user profiles.
The primary goal of cross-site tracking is to gather insights into user behavior and interests, allowing advertisers to deliver targeted ads based on the user's online activities. For example, if a user visits an online clothing store and later browses a news website, they may encounter ads for the same or similar clothing items they previously viewed. This personalized advertising is made possible by cross-site tracking, which enables advertisers to follow users across different websites and tailor their ad experiences accordingly.
While targeted advertising can be beneficial for businesses and users seeking relevant products or services, cross-site tracking raises significant privacy concerns. Users may feel that their online activities are being monitored without their consent, leading to a sense of intrusion and loss of control over their personal data. Furthermore, the accumulation of extensive user profiles across various websites can potentially expose sensitive information, posing risks to user privacy and security.
In response to these concerns, web browsers have implemented features to mitigate cross-site tracking. Safari, in particular, has taken proactive steps to limit the impact of third-party tracking on user privacy. By understanding the underlying mechanisms of cross-site tracking, users can make informed decisions about their online privacy and take advantage of the protective measures offered by Safari to enhance their browsing experience.
By shedding light on the intricacies of cross-site tracking, users can gain a deeper appreciation for the importance of privacy protection while navigating the digital landscape. This understanding empowers users to make conscious choices about their online activities and the tools they utilize to safeguard their personal information.
How Safari Prevents Cross-Site Tracking
Safari employs several strategies to prevent cross-site tracking and enhance user privacy. These measures are designed to limit the ability of third-party entities to track users across different websites, thereby reducing the collection of personal data without explicit user consent.
Intelligent Tracking Prevention (ITP)
Safari's Intelligent Tracking Prevention (ITP) is a key feature that targets cross-site tracking mechanisms. ITP uses machine learning algorithms to identify and block tracking techniques employed by third-party entities. By analyzing user interactions with websites and the storage of tracking data, ITP aims to restrict the effectiveness of cross-site tracking methods, such as persistent cookies and other tracking technologies.
Cross-Site Tracking Prevention
Safari's Cross-Site Tracking Prevention feature specifically focuses on limiting the cross-site tracking capabilities of third-party entities. By isolating the storage of website data and restricting the access of third-party domains to this data, Safari reduces the ability of advertisers and other entities to create comprehensive user profiles across multiple websites. This proactive approach disrupts the seamless tracking of user activities, thereby enhancing user privacy.
Enhanced Tracking Protection
Safari incorporates Enhanced Tracking Protection to bolster its defenses against cross-site tracking. This feature blocks known trackers and prevents them from monitoring user behavior across different websites. By proactively identifying and neutralizing tracking elements, such as scripts and cookies, Safari provides users with a more secure browsing environment, reducing the risk of unauthorized data collection and profiling by third-party entities.
Privacy Report
Safari's Privacy Report feature empowers users with insights into the tracking activities that are being blocked while browsing. By providing a comprehensive overview of the trackers that have been prevented from profiling user behavior, the Privacy Report enhances transparency and allows users to understand the impact of Safari's preventive measures. This visibility into tracking attempts reinforces user confidence in Safari's commitment to protecting their privacy.
By implementing these robust preventive measures, Safari demonstrates its dedication to safeguarding user privacy and mitigating the impact of cross-site tracking. These features collectively contribute to a more secure and privacy-conscious browsing experience, empowering users to navigate the web with confidence and peace of mind.
The proactive stance taken by Safari in preventing cross-site tracking underscores the browser's commitment to prioritizing user privacy and data security. By leveraging these built-in protective measures, users can enjoy a more privacy-respecting online experience while benefiting from the seamless functionality of Safari as their preferred web browser.
Enabling Prevent Cross-Site Tracking in Safari
Enabling the "Prevent Cross-Site Tracking" feature in Safari is a straightforward process that empowers users to take control of their online privacy and enhance their browsing security. By activating this feature, users can proactively limit the ability of third-party entities to track their activities across different websites, thereby reducing the collection of personal data without explicit consent.
To enable "Prevent Cross-Site Tracking" in Safari, users can follow these simple steps:
Open Safari Preferences : Begin by launching the Safari browser and accessing the "Preferences" from the Safari menu located in the top-left corner of the screen.
Navigate to Privacy Settings : Within the Preferences window, select the "Privacy" tab to access the privacy settings and options available in Safari.
Enable Prevent Cross-Site Tracking : In the Privacy tab, users will find the option to "Prevent cross-site tracking." Simply check the box next to this option to activate the feature.
Once "Prevent Cross-Site Tracking" is enabled, Safari will implement its preventive measures to limit the impact of cross-site tracking, bolstering user privacy and security during web browsing sessions. By isolating the storage of website data and restricting the access of third-party domains to this data, Safari disrupts the seamless tracking of user activities, thereby enhancing user privacy.
In addition to enabling "Prevent Cross-Site Tracking," users can also take advantage of Safari's other privacy features, such as Intelligent Tracking Prevention (ITP) and Enhanced Tracking Protection, to further fortify their browsing experience against intrusive tracking techniques.
By empowering users to enable "Prevent Cross-Site Tracking" and providing transparent insights into the tracking activities that are being blocked, Safari reinforces its commitment to prioritizing user privacy. This proactive approach aligns with Safari's dedication to offering a privacy-respecting browsing environment while maintaining the seamless functionality and user-friendly experience that users have come to expect from the Safari browser.
By taking control of their online privacy through the activation of "Prevent Cross-Site Tracking" and leveraging Safari's comprehensive privacy features, users can navigate the web with confidence, knowing that their personal data is being safeguarded and their privacy respected.
This simple yet impactful action empowers users to actively participate in shaping their online privacy and security, aligning with the evolving landscape of digital privacy concerns and the increasing demand for user-centric privacy protection measures.
Impact of Prevent Cross-Site Tracking on User Experience
Enabling the "Prevent Cross-Site Tracking" feature in Safari can significantly impact the overall user experience, particularly in terms of privacy, security, and browsing behavior. By actively mitigating the effects of cross-site tracking, Safari empowers users to navigate the web with enhanced confidence and control over their online interactions.

Enhanced Privacy and Security
The foremost impact of enabling "Prevent Cross-Site Tracking" is the bolstering of user privacy and security. With this feature activated, Safari diligently restricts the ability of third-party entities to monitor and track user activities across different websites. This proactive stance shields users from intrusive data collection and the creation of extensive user profiles without their explicit consent. As a result, users can engage in online activities with a heightened sense of privacy, knowing that their browsing behavior is not being extensively monitored and utilized for targeted advertising or profiling purposes.
Reduced Targeted Advertising
By limiting cross-site tracking, Safari's "Prevent Cross-Site Tracking" feature contributes to a reduction in targeted advertising based on users' browsing history and preferences. Users may notice a decrease in the frequency of personalized ads that follow them across various websites, resulting in a less intrusive and more organic browsing experience. This reduction in targeted advertising aligns with users' preferences for a less obtrusive online ad experience, allowing them to focus on content and interactions without feeling inundated by personalized marketing efforts.
User Empowerment and Control
Enabling "Prevent Cross-Site Tracking" empowers users to take an active role in shaping their online privacy and security. By making a conscious choice to limit cross-site tracking, users assert their control over the dissemination of their personal data and the extent to which their online activities are monitored by third-party entities. This sense of empowerment fosters a more positive and user-centric browsing experience, as users feel more in command of their digital interactions and the protection of their sensitive information.
Seamless Browsing Experience
Despite the enhanced privacy and security measures, enabling "Prevent Cross-Site Tracking" in Safari does not compromise the seamless functionality and user-friendly nature of the browsing experience. Users can continue to enjoy the full range of Safari's features and capabilities while benefiting from the protective measures that limit cross-site tracking. This balance between privacy protection and uninterrupted browsing ensures that users can navigate the web with ease and efficiency, without encountering unnecessary disruptions or limitations.
In essence, the impact of enabling "Prevent Cross-Site Tracking" on user experience is multifaceted, encompassing enhanced privacy, reduced targeted advertising, user empowerment, and a seamless browsing environment. By embracing this feature, users can cultivate a more privacy-respecting and secure online experience while leveraging Safari's comprehensive protective measures to navigate the digital landscape with confidence and peace of mind.
In conclusion, Safari's implementation of the "Prevent Cross-Site Tracking" feature represents a significant step towards prioritizing user privacy and security in the digital realm. By understanding the intricacies of cross-site tracking and the proactive measures employed by Safari to mitigate its impact, users can make informed decisions about their online browsing habits and take control of their personal data.
Enabling "Prevent Cross-Site Tracking" in Safari empowers users to actively participate in shaping their online privacy and security. The feature's impact extends beyond mere data protection, influencing the overall browsing experience by fostering a sense of empowerment, reducing targeted advertising, and maintaining a seamless user-centric environment.
Safari's commitment to privacy is further exemplified through features such as Intelligent Tracking Prevention (ITP), Enhanced Tracking Protection, and the provision of a Privacy Report, which collectively contribute to a more secure and transparent browsing experience. These measures align with the evolving landscape of digital privacy concerns and the increasing demand for user-centric privacy protection measures.
As users continue to navigate the web for various purposes, ranging from personal research to online transactions, the assurance of privacy and security becomes paramount. Safari's dedication to safeguarding user data and limiting intrusive tracking techniques underscores its commitment to providing a privacy-respecting browsing environment without compromising the seamless functionality and user-friendly experience that users have come to expect.
By embracing the "Prevent Cross-Site Tracking" feature and leveraging Safari's comprehensive protective measures, users can navigate the digital landscape with confidence, knowing that their personal data is being safeguarded and their privacy respected. This proactive approach aligns with the evolving landscape of digital privacy concerns and the increasing demand for user-centric privacy protection measures.
Ultimately, the integration of privacy-enhancing features in Safari reflects a broader industry shift towards prioritizing user privacy and data security. As users become more discerning about their online privacy, the availability of tools such as "Prevent Cross-Site Tracking" empowers them to take control of their digital footprint and engage in online activities with confidence and peace of mind.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Crowdfunding
- Cryptocurrency
- Digital Banking
- Digital Payments
- Investments
- Console Gaming
- Mobile Gaming
- VR/AR Gaming
- Gadget Usage
- Gaming Tips
- Online Safety
- Software Tutorials
- Tech Setup & Troubleshooting
- Buyer’s Guides
- Comparative Analysis
- Gadget Reviews
- Service Reviews
- Software Reviews
- Mobile Devices
- PCs & Laptops
- Smart Home Gadgets
- Content Creation Tools
- Digital Photography
- Video & Music Streaming
- Online Security
- Online Services
- Web Hosting
- WiFi & Ethernet
- Browsers & Extensions
- Communication Platforms
- Operating Systems
- Productivity Tools
- AI & Machine Learning
- Cybersecurity
- Emerging Tech
- IoT & Smart Devices
- Virtual & Augmented Reality
- Latest News
- AI Developments
- Fintech Updates
- Gaming News
- New Product Launches
Learn To Convert Scanned Documents Into Editable Text With OCR
Top mini split air conditioner for summer, related post, comfortable and luxurious family life | zero gravity massage chair, when are the halo awards 2024, what is the best halo hair extension, 5 best elegoo mars 3d printer for 2024, 11 amazing flashforge 3d printer creator pro for 2024, 5 amazing formlabs form 2 3d printer for 2024, related posts.
How To Allow Cross-Site Tracking In Safari On Mac
What Is Cross-Site Tracking In Safari

What Is Safari Privacy Report

How To Enable Third-Party Cookies On Safari

How To Restrict YouTube On Safari

How To Turn Off Cookies In Safari

Which Is Better: Safari Or Chrome

How To Clear Safari Cookies On IPhone
Recent stories.

Fintechs and Traditional Banks: Navigating the Future of Financial Services

AI Writing: How It’s Changing the Way We Create Content

How to Find the Best Midjourney Alternative in 2024: A Guide to AI Anime Generators

How to Know When it’s the Right Time to Buy Bitcoin

Unleashing Young Geniuses: How Lingokids Makes Learning a Blast!

- Privacy Overview
- Strictly Necessary Cookies
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

How to prevent cross-site tracking on your iPhone, iPad and Mac
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
- Click to share on Pinterest (Opens in new window)
As long as you’re online, your privacy is exposed. The good news is you can erase search history, visited websites, cookies and form data using private browsing mode. This means that anyone who uses the same computer as you won’t see your activity. Tap or click here for instructions on erasing your digital tracks .
Private browsing is good locally, but your activity can still be tracked online. And that data can be shared with third parties.
Different browsers offer various levels of privacy, and if you use Apple devices, you’re in luck. Apple’s built-in browser can block cross-site tracking, so you don’t have to worry about being followed. Here’s how to enable this critical privacy feature on your iPhone, iPad and Mac.
What is cross-site trafficking?
When you go from one website to another, you’re often followed by trackers that collect data on where you’ve been and what you’ve been doing. This data is used to create a profile on you that grows over time.
Your social media activity can also be tracked. For example, Facebook’s pixel-tracking technology lets website developers track Facebook users for ad targeting. Tap or click here for 10 Facebook privacy settings you need to change .
Data on your browsing habits, likes, shares, ads you click and shopping cart is all up for grabs. This can be sold to third parties or used for targeted advertising.
Using Safari on your Apple device, you can block cross-site trafficking with a simple setting.
RELATED: Yes, your data is for sale – Here’s what you can do to stop it
Prevent cross-site trafficking on your iPhone and iPad
Safari limits third-party cookies and data by default. It’s a good idea to ensure you have this option turned on. Here’s how:
- Go to Settings > Safari .
- Under Privacy and Security , toggle on Prevent Cross-Site Tracking . If it’s already on, then you’re good to go!
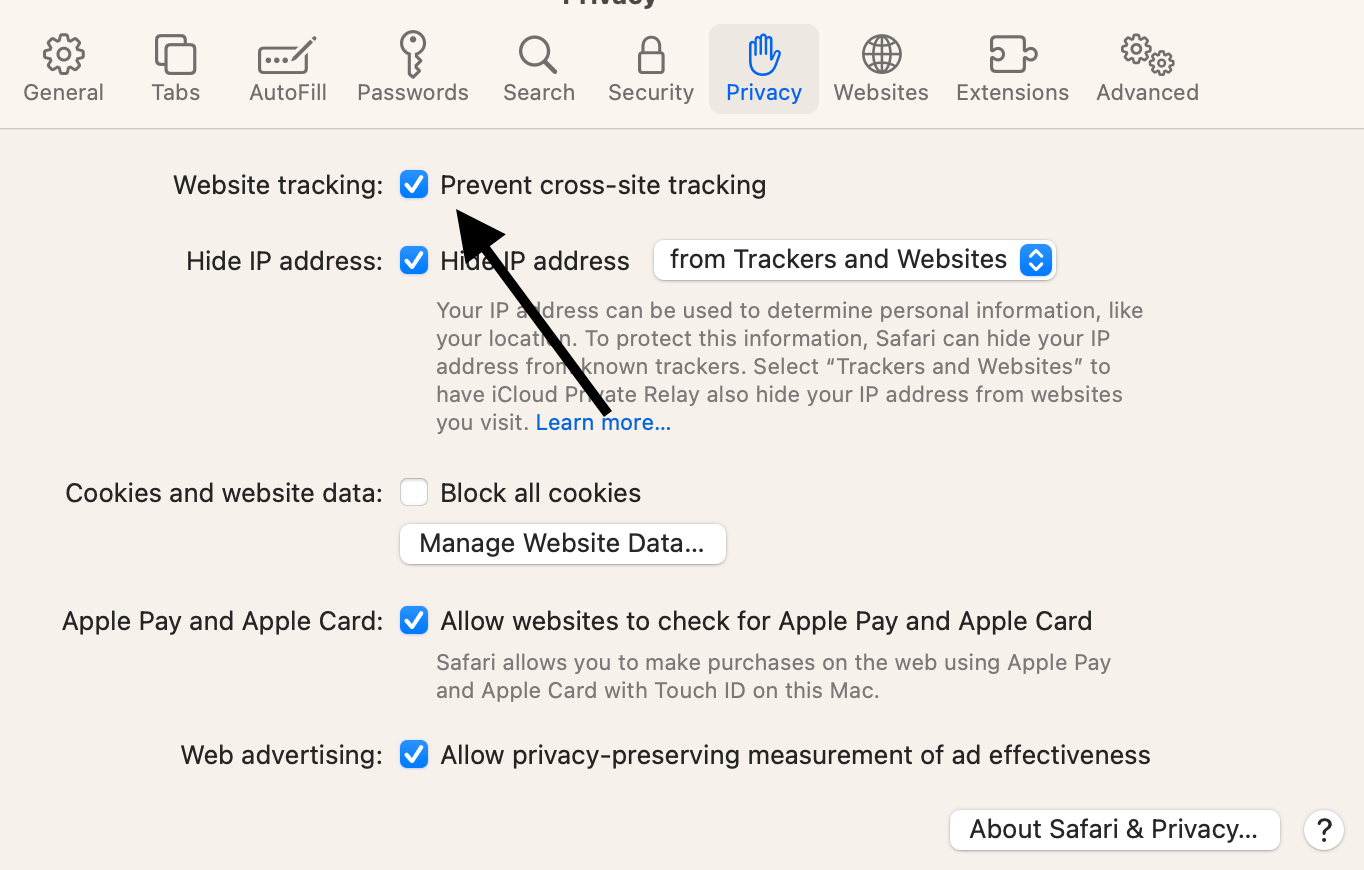
Prevent cross-site trafficking on your Mac
- Open the Safari app and go to Safari > Preferences > Privacy
- Next to Website tracking , check the box for Prevent cross-site tracking .
You may also like: Say goodbye to Google’s tracking – This Gmail alternative protects your privacy

Join the Komando Community
Get even more know-how in the Komando Community! Here, you can enjoy The Kim Komando Show on your schedule, read Kim's eBooks for free, ask your tech questions in the Forum — and so much more.
How-To Geek
How safari's new intelligent tracking prevention works.
It's one of the most discussed new features in High Sierra: Safari's new Intelligent Tracking Prevention.
Quick Links
What is cross-site tracking, what will intelligent tracking prevention actually do, how to turn off intelligent tracking prevention.
It's one of the most discussed new features in High Sierra : Safari's new Intelligent Tracking Prevention. Advertisers are upset about it , claiming it's "bad for the ad-supported online content and services consumers love." Apple is undeterred by the rhetoric . But what does the feature actually do?
Related: What's New in macOS 10.13 High Sierra, Available Now
Basically, Intelligent Tracking Prevention changes which sites can and can't use particular cookies, and in some cases deletes cookies that aren't doing anything useful for you. To quote the official explanation, from Apple's High Sierra feature list :
Remember when you looked at that green mountain bike online? And then saw annoying green mountain bike ads everywhere you browsed? Safari now uses machine learning to identify advertisers and others who track your online behavior, and removes the cross‑site tracking data they leave behind. So your browsing stays your business.
This sounds good in the abstract, but how does it actually work? Apple's official explanation on Webkit.org outlines the technology in language intended for developers; here's what users need to care about.
Intelligent Tracking Prevention works to prevent what's called cross-site tracking, a feature where a cookie served up by one website can track you across the wider web.
Why is this possible? Because when you load a web page not every element you see comes from the exact site you're looking at. Ads, for example, tend to come from third party ad networks, which might pull recently viewed items from Amazon, eBay, or other sites. Social media buttons are generally hosted by those social networks. Most sites make use of Google Analytics, and other tools to track user numbers.
It's part of how modern websites are built, and it's not a problem in and of itself. In some cases these third party services may access cookies stored by your browser, which also isn't a problem in and of itself.
In fact, many features useful rely on this. If you've ever used your Google or Facebook account to log into another site, you've used cross site cookies in a tangible way that makes your life easier.
That's why this is complicated: the cross site ads are creepy, but other cross site functionality makes the web a better place. How is a browser supposed to tell the difference?
So how will Intelligent Tracking Prevention actually work? Ironically, by tracking you---though all information stays on your machine, meaning nothing is uploaded to Apple. Safari will use your browsing history to work out which sites you're interested in, and use that information to save, partition, or delete cookies depending on context.
To Safari, domains you're interested in are domains you yourself visit on a regular basis. Domains you never visit directly, but regularly use cross site resources from, are deemed things you're not interested in. To quote the Webkit page again:
Let’s say Intelligent Tracking Prevention classifies example.com as having the ability to track the user cross-site. What happens from that point? If the user has not interacted with example.com in the last 30 days, example.com website data and cookies are immediately purged and continue to be purged if new data is added. However, if the user interacts with example.com as the top domain, often referred to as a first-party domain, Intelligent Tracking Prevention considers it a signal that the user is interested in the website and temporarily adjusts its behavior.
The behavior is relatively simple, so let's break it down:
- If you visit a domain directly, Safari will assume you're interested in the site, and will allow cross site tracking for the domain for 24 hours.
- If you then don't visit that domain for 24 hours, Safari will assume you've lost interest, and stop allowing cross site tracking for that domain.
- If you don't visit that domain for 30 days, Safari will delete the cookies for that domain entirely.
It's a little weird, so let's explore a concrete example. Let's say you're not a Facebook user, but occasionally click a Facebook link and read a public post. Under this scheme Facebook would be able to track your activity online using cookies for 24 hours, thanks to those "Like" buttons embedded on so many pages. After 24 hours Facebook would no longer be able to access these cookies, assuming you don't head to Facebook.com again. After 30 days of not visiting Facebook the cookie will be deleted completely.
Facebook is just one example of a site that uses cross site tracking, and this tracking is something regular Facebook users have learned to live with (if not love.) Ad networks aren't the same: they run completely in the background, and most people never visit their domains directly. Safari's Intelligent Tracking Prevention stops them from tracking you without breaking cookies for sites you actually use.
It makes sense when you think about it. Safari will keep cookies around for sites you regularly use, but quarantines and delete the cookies left there by advertisers and other tracking services. It's a compromise between functionality and privacy.
It's worth noting that Apple is uniquely positioned to offer such a feature. Google, for example, makes liberal use of cross-site tracking for its own ad network---Chrome users shouldn't hold their breath waiting for something similar on that browser.
Not sure you're a fan of this feature, or wonder if it's breaking a site you use regularly? It's easy enough to turn off. Open Safari, then click Safari > Preferences in the menu bar.
Related: How to Block Third-Party Cookies in Every Web Browser
Uncheck the top option, "Prevent cross-site tracking," and you're done. The feature is still turned off. You could block third party cookies in every browser instead, but know that this is far more likely to break sites than Safari's default method.
Photo Credit: Alejandro Escamilla , Jens Kreuter
- a. Send us an email
- b. Anonymous form
- Buyer's Guide
- Upcoming Products
- Tips / Contact Us
- Podcast Instagram Facebook Twitter Mastodon YouTube Notifications RSS Newsletter
Safari in iOS 11: Enabling Cross-Site Tracking Prevention to Protect Your Privacy
Safari in iOS 11 introduces a new tracking prevention feature that's meant to protect your privacy and make it harder for companies to track your browsing habits across multiple websites.
Disabling Cross-Site Tracking isn't going to cut down on the number of ads that you see, but it will make it harder for advertisers to gather data about what you've been browsing to deliver targeted ads. Here's how to enable it:
- Open the Settings app.
- Scroll down to Safari and tap it.
- Toggle it on so it's green.
This section of the Settings app also includes other Safari settings that are worth turning on if you haven't done so already, including "Ask Websites Not to Track Me," "Block Pop-ups," and "Fraudulent Website Warning." You can also restrict website access to cookies, the camera and microphone, and Apple Pay.
Get weekly top MacRumors stories in your inbox.
Top Rated Comments
I know I’m going against the grain here, but if we’re going to see ads anyway, I’d rather see ads about things that interest me or items that I’ve been shopping for lately. Isn’t that far better than seeing generic “Lose Your Belly Fat Using This 1 Weird Trick” garbage ads?!
Popular Stories

Apple Announces 'Let Loose' Event on May 7 Amid Rumors of New iPads
Apple Releases Open Source AI Models That Run On-Device

iOS 18 Rumored to Add These 10 New Features to Your iPhone

Apple Cuts Vision Pro Shipments as Demand Falls 'Sharply Beyond Expectations'

Apple Finally Plans to Release a Calculator App for iPad Later This Year
Next article.

Our comprehensive guide highlighting every major new addition in iOS 17, plus how-tos that walk you through using the new features.

App Store changes for the EU, new emoji, Podcasts transcripts, and more.

Get the most out your iPhone 15 with our complete guide to all the new features.
A deep dive into new features in macOS Sonoma, big and small.

Revamped models with OLED displays, M3 chip, and redesigned Magic Keyboard accessory.

Updated 10.9-inch model and new 12.9-inch model, M2 chip expected.

Apple's annual Worldwide Developers Conference will kick off with a keynote on June 10.

Expected to see new AI-focused features and more. Preview coming at WWDC in June with public release in September.
Other Stories

8 hours ago by Tim Hardwick

1 day ago by Joe Rossignol

1 day ago by MacRumors Staff

2 days ago by Joe Rossignol

3 days ago by Tim Hardwick
Iframing KB articles and Safari with "Prevent cross-site Tracking"
Our solution (Refined for Jira Cloud), has a feature, where we show Knowledge Base articles to authenticated users using iframes. This has worked fine, until Safari started blocking 3rd party cookies by default (the setting “Prevent cross-site Tracking”). Now the users using Safari get the error “The action performed requires a logged in user. Please log in and try again.”
Any suggestions for solving this?
The only solution I can think of, would be a new API, that provides the content of KB article, so that we can render it ourselves.
While this problem currently affects only Safari, FireFox and Chrome are expected to follow in a year or two.
For background, we fetch the KB article iframable url using servicedesk api (/rest/servicedeskapi/knowledgebase/article?query=article)
Hi @ErkkiLepre ,
Do you fetch the Knowledge Base article from your app’s iframe using AP.request('/rest/servicedeskapi/knowledgebase/article?query=article', ...) ( Request )?
I’m just trying to clarify which operation Safari is blocking. I think Safari has blocked cookies in iframes for quite some time now which is why we provide a Cookie JavaScript API .
Regards, Dugald
Hi @dmorrow
Thanks for the prompt response.
No, we get the iframe url using addon.httpClient in the backend.
Our solution is basically an external website, that fetches Jira/Confluence content using Atlassian API’s, and renders it. Displaying KB articles is an exception to this, as - and please correct me if I’m wrong - there’s no API for fetching the article content. That’s why we simply iframe it. But note, that the iframing happens from a non-atlassian domain.
If the “Prevent cross-site Tracking” feature is disabled in Safari, everything works fine, but when it’s enabled, Safari will not send the Atlassian session cookie, so the content will not be available (because it requires authentication).

Note the difference in the Request Cookies.
(The URL I’m iframing in this example is https://xxx.atlassian.net/rest/servicedeskapi/knowledgebase/article/view/416972801 )
When you say “the URL I’m iframing in this example is https://xxxx.atlassian.net/rest/servicedeskapi/knowledgebase/article/view/416972801 ”, do you mean the iframe URL is Knowledge base - Jira Service Management - Jira which is in turn sending a request to https://xxxx.atlassian.net/rest/servicedeskapi/knowledgebase/article/view/416972801 ?
Have you tried setting the allow-same-origin sandbox option for the iframe? e.g. <iframe sandbox="allow-same-origin"...
No, the iframe url is https://xxxx.atlassian.net/rest/servicedeskapi/knowledgebase/article/view/416972801

As a heads up, the Service Desk team have been looking into this.
Hi again. Any update on this?
The Service Desk team are still looking into this, but I’m not exactly sure what course of action they are taking. I’ll check if it is possible for them to provide more details.
At the moment in order to Prevent cross-site Tracking, webkit strips the third-party cookies away before sending requests to Atlassian’s public APIs as you already noticed (the third-party cookies here are the ones created after a user is authenticated by Jira).
There are a few limitations specifically to KB articles because all the subsequent requests required to load a KB article also relies on the cookies mentioned in this thread. This demands changes in the way the content for KB articles are retrieved in terms of authentication, so there’s no workaround available at the moment.
I’ve created a public ticket to address this issue and to help all vendors and users to track the next steps to solve this: [JSDCLOUD-9287] Third-party cookie blocking in Safari - Create and track feature requests for Atlassian products.
Regards, Adolfo Eloy
Thanks for the help @AdolfoEloy and @dmorrow .
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Prevent cross-site tracking is greyed out
I've read articles that describe why the prevent cross-site tracking button may be grayed out. I do not fit into any of the categories. The only thing I can think of is that I did have an employer gmail account last year, but no longer have that account. I'm on the latest iOS. How can I restore the button function?
Posted on Mar 23, 2023 6:33 AM
Posted on Mar 24, 2023 1:14 PM
Hello 444sync,
We see that you have questions about Cross-Site Tracking on your iPhone. You can learn more about the feature here: Browse privately in Safari on iPhone - Apple Support
After testing on our device, it looks like Cross-Site Tracking can be greyed out if you have Block All Cookies enabled. You can learn how to block cookies here: Clear the history and cookies from Safari on your iPhone, iPad, or iPod touch - Apple Support
If that's not it, do you have Screen Time enaled on your iPhone? Screen Time restrictions can stop you from making changes in Settings. Use Screen Time on your iPhone, iPad, or iPod touch - Apple Support
Another thing to check for is a profile. Profiles can also stop you from making changes in Settings. Install or remove configuration profiles on iPhone - Apple Support
Similar questions
- Toggle Allow Apps to Request to Track OFF If I toggle Allow Apps to Request to Track OFF it will not allow any app to ask permission and block them from tracking, Correct? Like in the screenshot? 508 7
- Where is the “new page” button? I do not see it anywhere on the website page. Where is the “new page” button to turn off private browsing? I do not see it anywhere on the website page. 137 1
- Tracking on settings I go to my settings to turn on my tracking request for apps and the toggle button in grey and not letting me switch it and it is saying that a profile is restricting it what do I do?!?!?!?!? 550 1
Loading page content
Page content loaded
Mar 24, 2023 1:14 PM in response to 444sync
Mar 26, 2023 9:56 PM in response to 444sync
Thank you, it was the cookies! Working fine now... but, that leads to yet another issue: how my iPhone X randomly toggles buttons on and off. I'll have to post that question elsewhere! Appreciate the fix.
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Safari blocks cookies for iFrame domain when domain doesn't match source website #18530
Starker3 commented Dec 22, 2021
- 👍 2 reactions
- 🎉 1 reaction
bastos71 commented Jan 24, 2022 • edited
Sorry, something went wrong.
tsteur commented Jan 25, 2022
Findus23 commented Mar 6, 2022
heurteph-ei commented Apr 26, 2022
Findus23 commented apr 26, 2022.
TechDad3949 commented May 9, 2022
sandeepks230 commented Sep 20, 2022
justinvelluppillai commented Nov 4, 2022
No branches or pull requests
Safari User Guide
- Change your home page
- Import bookmarks, history and passwords
- Make Safari your default web browser
- Go to websites
- Find what you’re looking for
- Bookmark web pages that you want to revisit
- See your favourite websites
- Use tabs for web pages
- Pin frequently visited websites
- Play web videos
- Mute audio in tabs
- Pay with Apple Pay
- Autofill credit card info
- Autofill contact info
- Keep a Reading List
- Hide ads when reading articles
- Translate a web page
- Download items from the web
- Share or post web pages
- Add passes to Wallet
- Save part or all of a web page
- Print or create a PDF of a web page
- Customise a start page
- Customise the Safari window
- Customise settings per website
- Zoom in on web pages
- Get extensions
- Manage cookies and website data
- Block pop-ups
- Clear your browsing history
- Browse privately
- Autofill username and password info
- Prevent cross-site tracking
- View a Privacy Report
- Change Safari preferences
- Keyboard and other shortcuts
- Troubleshooting
Prevent cross-site tracking in Safari on Mac
Some websites use third-party content providers. You can stop third-party content providers from tracking you across websites to advertise products and services.
Open Safari for me
Select “Prevent cross-site tracking”.
Unless you visit and interact with the third-party content provider as a first-party website, their cookies and website data are deleted.
Social media sites often put Share, Like or Comment buttons on other websites. These buttons can be used to track your web browsing — even if you don’t use them. Safari blocks that tracking. If you still want to use the buttons, you’ll be asked for your permission to allow the site to see your activities on the other websites.
For a Privacy Report that shows a list of known trackers who’ve been blocked from tracking you, see See who was blocked from tracking you .
Note: Every time you visit a website, it gathers data about your device — such as your system configuration — and uses that data to show you a web page that works well on your device. Some companies use this data to try to uniquely identify your device — known as fingerprinting . To prevent this, whenever you visit a web page, Safari presents a simplified version of your system configuration. Your Mac looks more like everyone else’s Mac, which dramatically reduces the ability of trackers to uniquely identify your device.
PSA: Safari 13 - breaking iframes due to "cross-site tracking" disabled
Recently some of our iframes were breaking in clients’ websites.
These were bubble pages built into their sites using an iframe. They have been working fine for a long time.
They stopped working for Safari users on desktop and mobile. There’s a setting in Safari that’s comes pre-checked now, “Prevent cross-site tracking”. That breaks iframes that are hosted outside of the website’s domain if they utilize workflows in many cases.
I encourage anybody utilizing iframes out in the wild to run a full pass using Safari on desktop/mobile and double-check that your iframes still work.
In my case, I enabled the GDPR-compliance setting found in bubble’s settings and it fixed the issue. Most iframes (at least the ones I create) don’t require a user to log in, etc. Just fill out a form and submit. Enabling the GDPR removes bubble’s reliance on cookies for processing workflows and should fix your iframe on Safari.
Huge shoutout to Jeff Thill from Team Bubble for pointing me in the right direction. I hope this helps somebody else!
Where exactly is this?

IMAGES
VIDEO
COMMENTS
How to Enable Safari Prevent Cross-Site Tracking. As mentioned, Prevent Cross-Site Tracking is typically enabled by default on iOS 16. If, for whatever reason, you suspect it may be off, you can find the option to turn it on here: Open your Settings app. Navigate to Safari. Scroll down until you find 'Prevent Cross-Site Tracking' in the ...
Note: Every time you visit a website, it gathers data about your device—such as your system configuration—and uses that data to show you a webpage that works well on your device.Some companies use this data to try to uniquely identify your device—known as fingerprinting.To prevent this, whenever you visit a webpage, Safari presents a simplified version of your system configuration.
I would like to detect when Prevent Cross-site tracking is active in a browser using JavaScript. My challenge is trying to find a method to detect this and show a warning popup to the user when this cross-site tracking is disabled by a users browser. This became essential after Safari 13 disabled it as default.
A key term here is cross-site. This means that the top privately-controlled domain name of the <iframe> is different from that of the parent page. In the examples below, the top privately-controlled domain name is in italics. www. simoahava.com. www. gtmtools.com. www. ebay.co.uk. sahava.github.io.
In the case of Safari and WebKit, using the Storage Access API enables cookie access under Intelligent Tracking Prevention. ... In shipping Safari, your cross-site iframe that is about to request storage access must be a direct child frame of the top frame. Nested iframes can request storage access as of iOS 14.5 and macOS 11.3 (currently in beta).
Safari has an important privacy feature to prevent cross-site tracking. Regardless of your device — Mac, iPhone, iPad or Windows PC — you will see an option to turn off or on this feature in Safari's settings.
For even more info, you can click the Information (i) button to open a detailed report from the past 30 days. The Trackers prevented from profiling you section at the top of the report displays the number of trackers Safari recently thwarted. Additionally, Websites that contacted trackers shows the percentage of sites that attempted to track you. You can either opt to view a list of Websites ...
One such browser, Safari, has introduced a feature called "Prevent Cross-Site Tracking" to enhance user privacy and security. This feature aims to limit the ability of advertisers and other entities to track users across different websites, thereby reducing the collection of personal data without consent. Understanding the mechanisms behind ...
I want to enable cross-site tracking for a specific web site where I need it, and keep it disabled for all other sites. How do I do this? In the Preferences all I can see is a single checkbox to turn it on or off for the whole browser. I looked at "Settings for this website", but the option for cross-site tracking doesn't appear there.
Prevent cross-site trafficking on your iPhone and iPad. Safari limits third-party cookies and data by default. It's a good idea to ensure you have this option turned on. Here's how: Go to ...
Open Safari, then click Safari > Preferences in the menu bar. Related: How to Block Third-Party Cookies in Every Web Browser. Uncheck the top option, "Prevent cross-site tracking," and you're done. The feature is still turned off.
Here's how to enable it: Open the Settings app. Scroll down to Safari and tap it. Scroll down to "Prevent Cross-Site Tracking." Toggle it on so it's green. This section of the Settings app also ...
iframe not working with safari. I am using cross domain implementation for which on page of Site A, I load iframe with Site B. Page inside iFrame calls rest apis of Site B and loads other pages from Site B depending upon responses. Although while loading these responses I am getting errror as "Cookies are not turned on in your browser".
That's why we simply iframe it. But note, that the iframing happens from a non-atlassian domain. If the "Prevent cross-site Tracking" feature is disabled in Safari, everything works fine, but when it's enabled, Safari will not send the Atlassian session cookie, so the content will not be available (because it requires authentication).
After testing on our device, it looks like Cross-Site Tracking can be greyed out if you have Block All Cookies enabled. You can learn how to block cookies here: Clear the history and cookies from Safari on your iPhone, iPad, or iPod touch - Apple Support
Our booking widgets are provided to our customers who then embed them on their on websites in what is called an iFrame. ... and Safari 14 on MacOS have introduced new privacy features including a more aggressive approach to preventing cross-site tracking. How to disable cross-site tracking prevention for iPhone & iPad ... Uncheck the Prevent ...
It seems that the recent updates to the Safari browser (Prevent cross-site tracking) blocks any cookies from being generated when the Matomo domain doesn't match the website it's being loaded from. This breaks the use of iFrames for Matomo that require cookies to be set (For example the logme feature)
Note: Every time you visit a website, it gathers data about your device — such as your system configuration — and uses that data to show you a web page that works well on your device.Some companies use this data to try to uniquely identify your device — known as fingerprinting.To prevent this, whenever you visit a web page, Safari presents a simplified version of your system configuration.
Safari flat out doesn't let you set cookies in iframes of domains different than the parent domain, server-side CORS headers be damned. To clarify: user is on domainA.com. An iframe for domainB.com is open, and attempts to authenticate the user on domainB.com inside the iframe. Set-Cookie header is returned from the server inside the domainB ...
There's a setting in Safari that's comes pre-checked now, "Prevent cross-site tracking". That breaks iframes that are hosted outside of the website's domain if they utilize workflows in many cases. I encourage anybody utilizing iframes out in the wild to run a full pass using Safari on desktop/mobile and double-check that your iframes ...